See below for how to create an issuing CA after Creating an online root CA.
To create an issuing CA
- Navigate to Administration > PKIaaS Management.
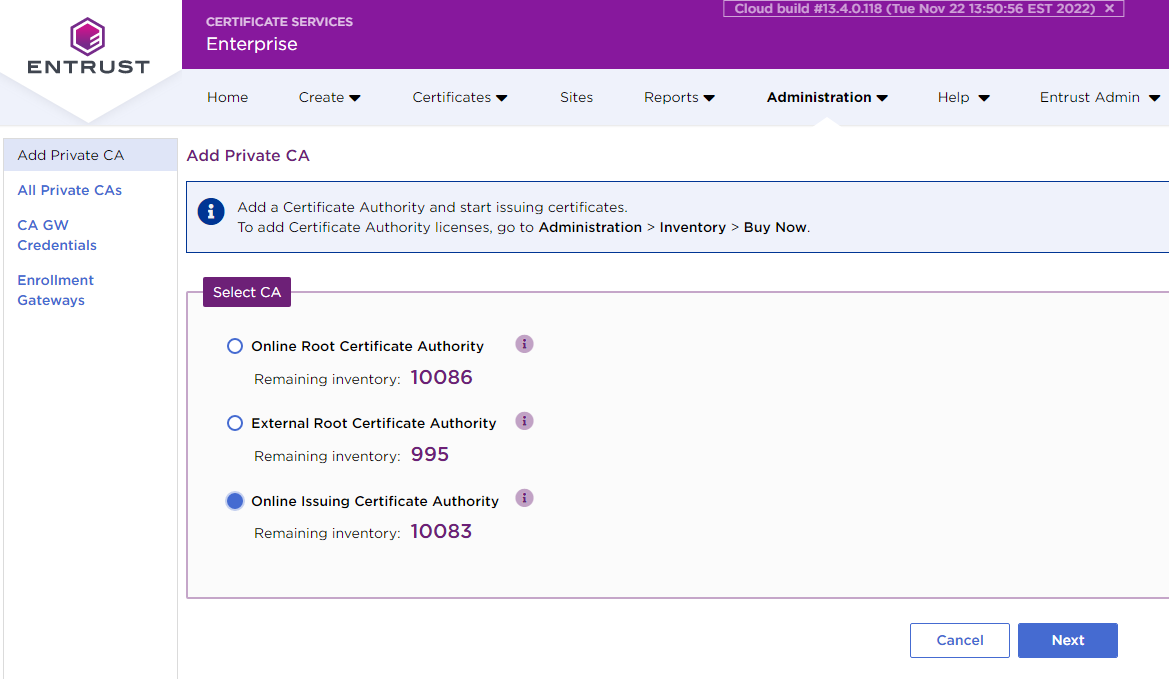
- In the side pane, click Add Private CA.
- In Select CA, choose Issuing Certificate Authority.
- Click Next to display the CA Information screen.
- Enter the values described below.
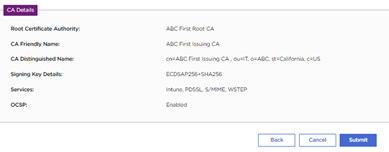
- Click Next to review the CA information.
- Click Submit.
- In the confirmation request, click OK to start the CA creation process.
- When the CA creation completes, check the CA details in the CA grid view.
- Refresh the grid. You will notice that the status changes to Active.
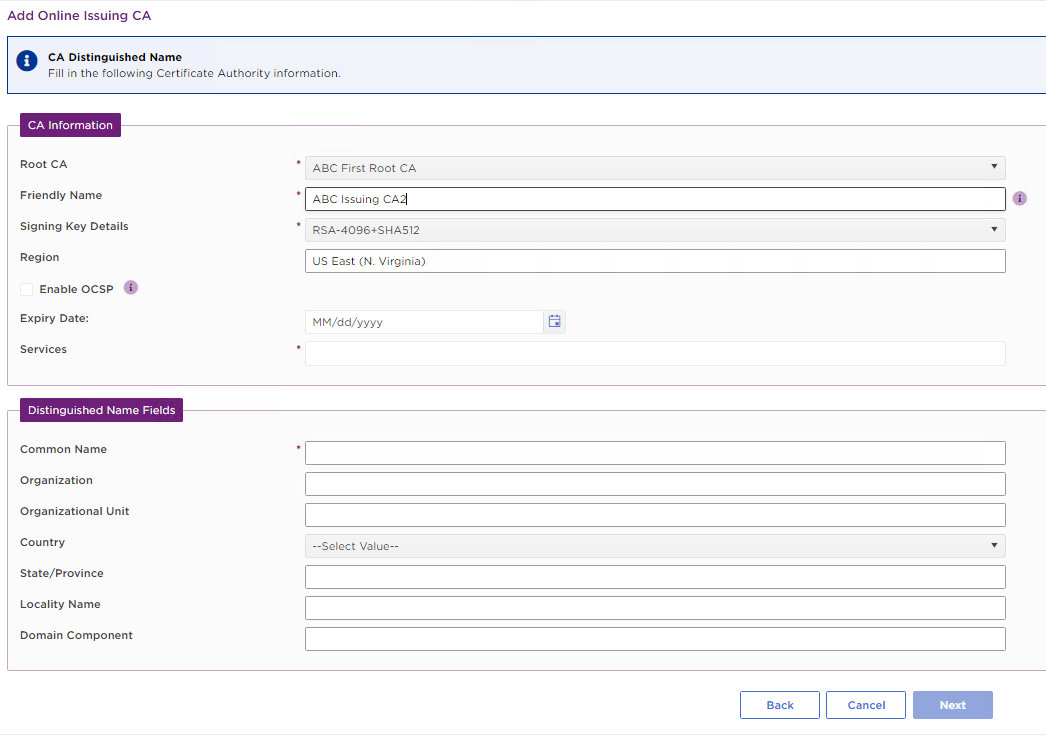
Root CA
Select the CA created in Creating an online root CA.
Mandatory: Yes.
Friendly Name
Enter an informal name for the new CA.
Mandatory: Yes.
Signing Key Details
Select one of the algorithms described in Certification Authority instantiation.
Mandatory: Yes.
Region
This view-only field displays the region of the root CA.
You cannot change the region for an issuing CA. The region of the issuing CA will be decided by the region of the root CA that signs the issuing CA.
Enable OCSP
Check box if you want to enable OCSP for this issuing CA.
You cannot change this setting after provisioning the CA.
Mandatory: No.
Expiry Date
Select the expiry date for the CA certificate. Use the date picker or enter a date in the following format.
mm/dd/yyyyThe expiry date of an issuing CA must be earlier than the expiry date of the root CA.
Mandatory: No. If you do not assign a specific expiry date, the expiry period defaults to 10 years for issuing CAs.
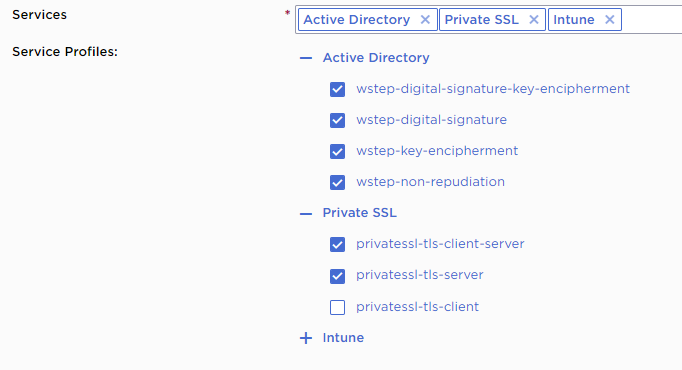
Services
Select a predefined set of certificate profiles. For example,
- Select Intune for Automating Intune enrollment with an Entrust-hosted Enrollment Gateway.
- Select Active Directory for Automating enrollment with an on-premises Enrollment Gateway and WSTEP.
Service Profiles
In this field:
- Click + to display the profiles supported by each service.
- Activate or deactivate each profile by checking or unchecking the corresponding box.
See below for a reference of the supported profiles.
- Active Directory (WSTEP) certificate profiles
- CMPv2 certificate profiles
- Code signing certificate profile
- eSIM certificate profiles
- EST certificate profiles
- Intune certificate profiles
- MDMWS certificate profiles
- Mobile device certificate profile
- Multiuse certificate profiles
- Private SSL (ACMEv2) certificate profiles
- S_MIME certificate profiles
- SCEP certificate profiles
- Smartcard certificate profiles
- V2G certificate profiles
Mandatory: No.
Distinguished Name Fields
Enter a value for each field in the Distinguished Name of the CA certificate.
Mandatory: Only the Common Name certificate field.