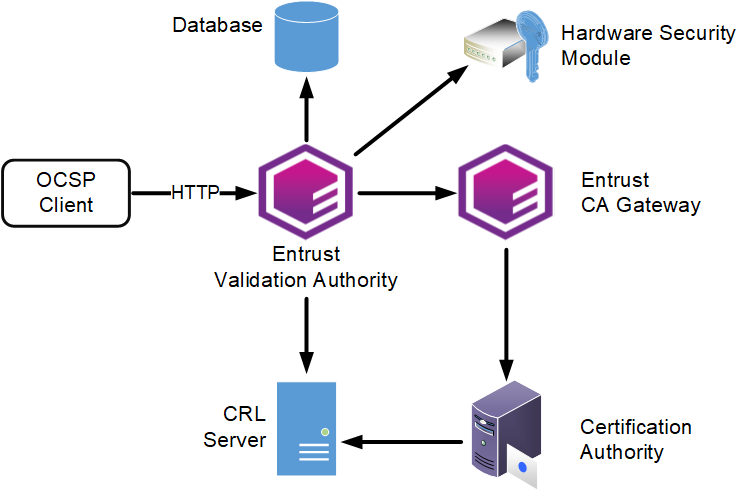
The Entrust Validation Authority (EVA) solution responds to OCSP requests on the validation status of the certificates issued by a Certificate Authority. To respond to these requests, the Entrust Validation Authority solution connects with different components.
See below for a description of each component.
OCSP client
Multiple clients send OCSP requests to the OCSP Responder service of the Entrust Validation Authority solution.
Certificate Authority
The Entrust Validation Authority solution checks the status of certificates issued by one or multiple Certificate Authorities (CAs).
As explained in Starting up Certificate Authorities, the Certificate Authorities solution provides built-in CRL and OCSP services. Therefore, you do not need an Entrust Validation Authority for CAs created with the Certificate Authorities solution.
Certificate information source
Through Entrust CA Gateway, Entrust solutions obtain a direct feed of issued certificates from each supported Certificate Authority (CA). See the following table for the CA Gateway deployment required by each type of CA.
CA type | CA Gateway deployment |
|---|---|
Certificate Authority running on PKI Hub | Create a Certificate Authority instance, as explained in Starting up Certificate Authorities, and select the built-in CA Gateway service of this CA. |
External Certificate Authority | Start up the Entrust CA Gateway solution and connect it with the external CA as explained Starting up CA Gateway. |
Alternatively, the Entrust Validation Authority solution can obtain revocation information from a full or "combined" CRL published in an LDAP or HTTP server.
Entrust Validation Authority does not support partitioned CRLs.
Hardware Security Module
A Hardware Security Module (HSM) manages one or several OCSP signing keys.
Database.
A database stores the status of the certificates.